Information
Exchange Team Blog – Released: March 2021 Exchange Server Security Updates
March 2021 Exchange Server Security Updates for older Cumulative Updates of Exchange Server
My Actions
“Locking my doors”
1 – Putting the Exchange Server into DAG Maintenance Mode
2 – Installing the most recent Cumulative Update (run as Administrator)
3 – Temporarily disable file-level antivirus software
4 – Installing the Security Patch by opening up a Run as Administrator CMD and running the file via elevated command prompt – VERY IMPORTANT TO RUN IT THIS WAY)
5 – After the installation is finished, re-enable the antivirus software, and then restart the computer. (You might be prompted by the installer to restart.)
You can confirm that your server is patched by running the HealthChecker.ps1 script inside an elevated Exchange Management Shell window.
I ran the Test-ProxyLogon.ps1 CSS-Exchange/Security at main · microsoft/CSS-Exchange (github.com) and found suspicious activity. Note that this script has been updated. It is now saving the results in .csv and .log files in the Test-ProxyLogonLogs subdirectory of the directory that you ran the script in:

(Click the output above to see it enlarged.)
“Kicking them out of my house”
Then, I followed the instructions on Microsoft Exchange Server Vulnerabilities Mitigations – updated March 6, 2021 – Microsoft Security Response Center by downloading MSERT and running a FULL SCAN on the Exchange Server that showed the suspicious activity. Make sure you are in Maintenance Mode when running this! The scanner uses 100% of CPU.
This tool is constantly being updated. Every time you plan to run the MSERT download a new copy so that you have the most up-to-date information.
That resulted in finding an exploit and removing it (kicking them out of my house):
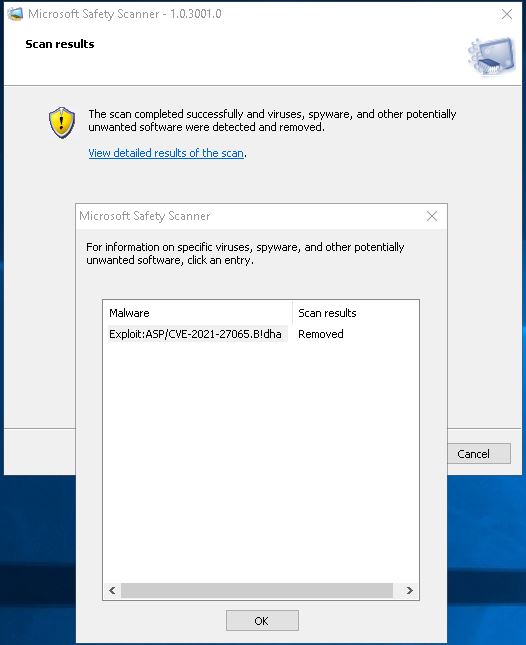
Clicking the link (under Malware) brought me to: Exploit:ASP/CVE-2021-27065.B!dha threat description – Microsoft Security Intelligence
After this action was taken, I took the server out of Maintenance Mode.
Average Time to Complete Tasks
- 10 minutes – Putting the Exchange Server into DAG Maintenance Mode
- 60 minutes – Installing the most recent Cumulative Update (run as Administrator)
- 5 minutes – Reboot
- 5 minutes – Temporarily disable file-level antivirus software
- 35 minutes – Installing the Security Patch by opening up a Run as Administrator CMD and running the file via elevated command prompt – VERY IMPORTANT TO RUN IT THIS WAY)
- 5 minutes – Reboot
- 5 minutes – After the installation is finished, re-enable the antivirus software, and then restart the computer. (You might be prompted by the installer to restart.)
- 5 minutes – Running Test-ProxyLogon.ps1
- 90 minutes – Running MSERT
- 10 minutes – Taking the Exchange Server out of DAG Maintenance Mode
- 10 minutes – Quick checks of Exchange Server and Event Log review
- 4:00 Hours Total per Server
Additional Checks
I also checked and no suspicious new accounts have been created in the last 10 days (covering the dates listed in the Test-ProxyLogon.ps1 result).
PowerShell on Server with AD module:
$DateCutOff=(Get-Date).AddDays(-10)
Get-ADUser -Filter * -Property whenCreated | Where {$_.whenCreated -gt $datecutoff} | FT Name, whenCreated -Autosize
I finally checked for suspicious new LOCAL users and suspicious membership in LOCAL groups on the Exchange Server:
Start > Run > lusrmgr.msc
Still on Exchange Server 2010?
The steps in the article apply to Exchange Server 2013 – 2019. If you have Exchange Server 2010 in your environment, install the Exchange Server 2010 SP3 Update Rollup 32 instead of steps 2 and 3 at the top of this article.
